Security professionals are widely adopting MITRE ATT&CK™ for network threat hunting. ATT&CK stands for Adversarial Tactics, Techniques and Common Knowledge, and it represents a globally accessible information base of adversary tactics and techniques based on real-world observations. MITRE ATT&CK provides several benefits for security teams.
Network Threat Hunting with MITRE ATT&CK
MITRE ATT&CK provides a common language, which describes threat tactics and techniques across the enterprise, that is useful for all roles in a security organizations, from CISOs to security analysts. There is tremendous value in using MITRE ATT&CK and its associated matrices with automated detection and network threat hunting capabilities. That’s why we integrated the MITRE ATT&CK framework natively into our network threat detection and response platform.
Network Threat Hunting with a Built-in MITRE ATT&CK Engine
To date, security vendors have used the MITRE ATT&CK framework to demonstrate the efficacy of their product. Vendor A, for example, might claim how their product covers X% of the endpoint tactics and techniques. Meanwhile, Vendor B might stake claims around coverage for network tactics and techniques. Well, here’s the deal:
While some vendors may use MITRE ATT&CK as a point of reference, MistNet Network Detection and Response (NDR) by LogRhythm is the first and only threat detection and hunting platform to integrate the MITRE ATT&CK matrix natively into the product. MistNet NDR also delivers broad coverage and defense for a complete set of endpoint and network tactics as defined by MITRE ATT&CK.
MistNet NDR provides an intuitive visualization of the Enterprise ATT&CK Matrix and shows any threats detected in your enterprise and their respective mappings to ATT&CK tactics and techniques in real time to simplify network threat hunting.
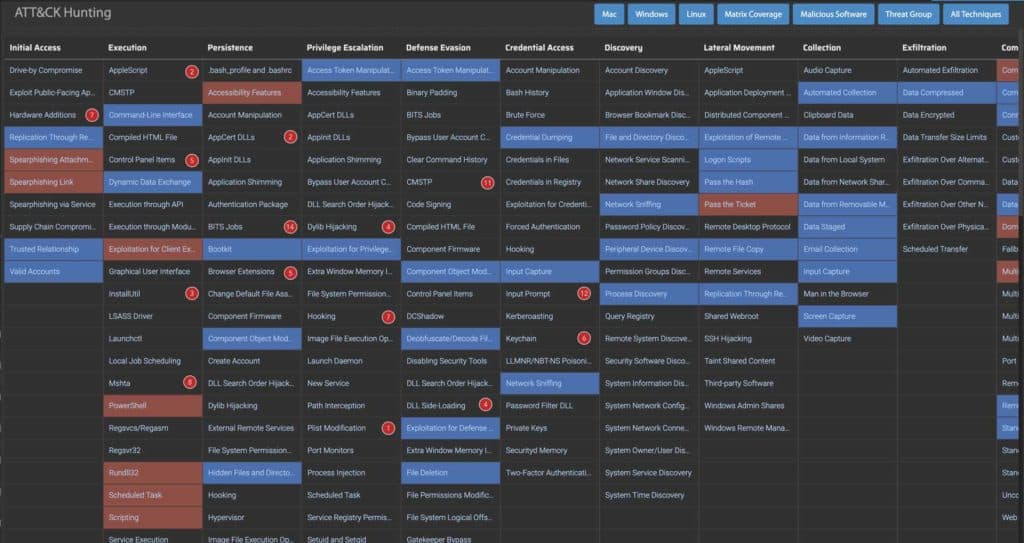
Figure 1: Enterprise ATT&CK Matrix in MistNet NDR
MistNet NDR also integrates a Threat Group view that allows you to see groupings of tactics and techniques mapped to various known threat groups. So, say you want to see if the threat group Comment Panda is in your network or the Dynamite Panda threat. Click on APT1 and APT18 in the Threat Group window, and the tactics and techniques associated with those threat groups will instantly light up and show any anomalies or vulnerabilities detected.
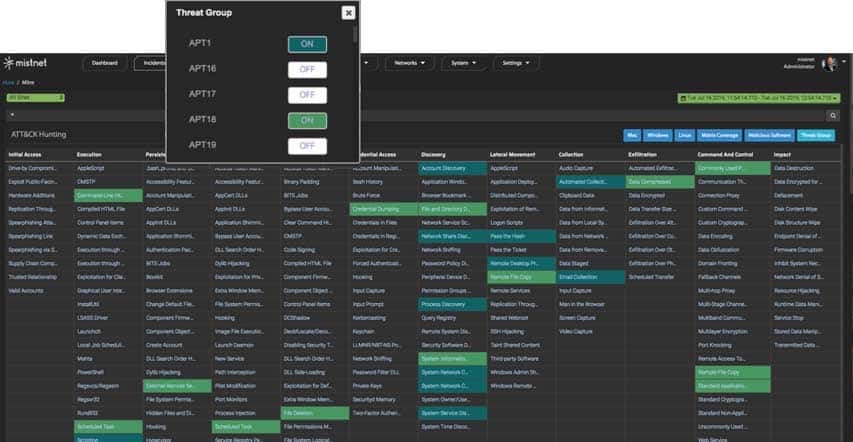
Figure 2: Threat Group view in MistNet NDR
The integrated MITRE ATT&CK engine also serves as an effective foundation for compliance and audit checks. Security teams can run exercises against specific tactics or techniques to measure efficacy of security practices. Teams can also perform real-time network threat hunting exercises with the built-in MITRE ATT&CK engine, looking for vulnerabilities or gaps with just a few clicks. And with this, your team is empowered with a data-driven approach to prioritizing and scaling cybersecurity programs, practices, and budgets.
Get Started with Machine Learning-Driven Network Threat Detection and Response
MistNet NDR by LogRhythm provides a machine learning (ML)-driven network detection and response (NDR) solution helps you detect threats like lateral movement, exfiltration, malware compromise, and ransomware in real time. Combined with a built-in MITRE ATT&CK engine, MistNet NDR eliminates blind spots and maximize your network threat detection capabilities.
Schedule a demo today to see how LogRhythm’s SaaS security information and event management (SIEM) platform and MistNet NDR can enhance your deep network visibility, behavior analytics and threat detection capabilities.
The post Network Threat Hunting Made Easy With the MistNet NDR MITRE ATT&CK™ Engine appeared first on LogRhythm.
*** This is a Security Bloggers Network syndicated blog from LogRhythm authored by Angela Romero. Read the original post at: https://logrhythm.com/network-threat-hunting-made-easy-with-the-mistnet-ndr-mitre-attck-engine/
February 27, 2021 at 08:18AM
https://securityboulevard.com/2021/02/network-threat-hunting-made-easy-with-the-mistnet-ndr-mitre-attck-engine/
Network Threat Hunting Made Easy With the MistNet NDR MITRE ATT&CK™ Engine - Security Boulevard
https://news.google.com/search?q=easy&hl=en-US&gl=US&ceid=US:en
No comments:
Post a Comment